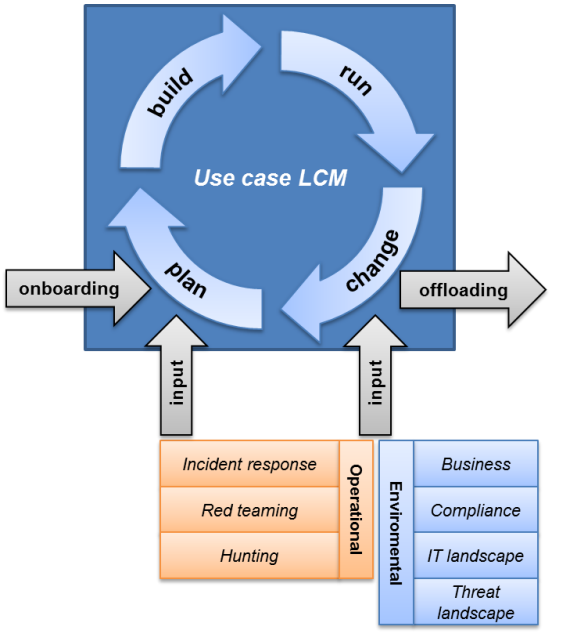
The Security Operations Center (SOC) is pivotal in protecting an organization’s digital assets, acting as the nerve center for detecting, investigating, and responding to cybersecurity threats. However, the SOC’s effectiveness is drastically improved with well-defined use cases to guide its operations. A use case provides the SOC with a focused, structured scenario or specific problem to address, ensuring its activities align with the organization’s unique threat landscape and security priorities.
Use cases are the foundation for the SOC’s day-to-day operations, helping analysts prioritize threats, fine-tune detection mechanisms, and streamline response efforts. They transform the SOC from a reactive entity—merely responding to incidents as they arise—into a proactive force capable of anticipating potential security challenges and taking preemptive measures. Without this structured approach, the SOC risks becoming overwhelmed, directionless, and inefficient, responding to every alert without a clear sense of priority or strategic focus.
However, defining, implementing, testing, and continuously refining these use cases is far more complex than it may initially appear. Effective use cases require a deep understanding of the organization’s business processes, threat models, and risk tolerance. It also involves constant adaptation to an ever-evolving cyber threat landscape, where new attack vectors and vulnerabilities emerge regularly. Use cases must be validated through rigorous testing to ensure they work as intended and are regularly reassessed to account for changes in the organization’s environment and the external threat landscape.
This ongoing process demands a combination of technical expertise, cross-functional collaboration, and strategic foresight, making it one of the most challenging yet critical aspects of SOC management. Cross-functional collaboration is particularly important, as it ensures that use cases are aligned with the organization’s overall security strategy and business objectives.
- Complexity of Security Threats: The landscape of cybersecurity threats constantly evolves, becoming more sophisticated and more complex to predict. Defining use cases that account for the broad spectrum of possible attacks requires deep expertise, comprehensive threat intelligence, and foresight into how attackers operate. It’s not enough to plan for known threats; SOC teams must anticipate the unknown, which complicates creating relevant use cases.
- Integration with Business Objectives: A SOC’s activities must align with the organization’s broader business goals and risk management strategies. This requires a deep understanding of the most critical assets, how they align with business operations, and how potential attacks might disrupt these processes. The challenge lies in translating complex technical threats into business risks and developing use cases that prioritize protection accordingly.
- Dynamic Technology Environment: As organizations adopt new technologies and shift to cloud-based or hybrid environments, the SOC must adapt its monitoring and response capabilities. Use cases must evolve alongside this dynamic technology environment, which involves constant reassessment and adaptation. It can be difficult and time-consuming to keep up with emerging technologies and integrate them into use case development.
- Collaborative Challenges: Effective use cases involve collaboration between security teams, IT departments, and business stakeholders. Miscommunication between these groups can lead to better-defined or relevant use cases. Additionally, if business leaders and IT teams don’t understand the SOC’s capabilities or language, the collaboration becomes even more challenging, leading to friction.
- Resource and Skill Constraints: Even when the correct use cases are identified, implementing, testing, and validating them requires the right resources and skills. Many SOCs need help with staffing shortages, skill gaps, or overworked teams, making it challenging to dedicate time and focus on refining use cases effectively. Testing and validating use cases also involve creating simulations or leveraging threat intelligence, requiring specialized knowledge.
- Continuous Reassessment: The cybersecurity environment is dynamic, and what works today may be obsolete tomorrow. Use cases must be continuously reassessed and updated to keep pace with emerging threats, technological changes, and organizational risk profile shifts. This ongoing process can be labor-intensive, and organizations that don’t prioritize reassessment may leave their SOC working with outdated or irrelevant use cases.
Strategic alignment
A common challenge in cybersecurity organizations is the disconnect between strategic security planners and SOC operators. While decision-makers often have a broad, high-level view of the organization’s security needs, they may propose use cases that, although seemingly innovative or aligned with current trends, must align with the practical realities of day-to-day SOC operations. These proposals can be driven by the desire to adopt cutting-edge technologies or methodologies that sound impressive on paper but lack the necessary context and relevance to the organization’s actual threats.
This disconnect is often rooted in a fundamental gap between those who set the security agenda—typically, executives and high-level strategists—and those responsible for executing it. SOC operators in the trenches dealing with real-time threats, incidents, and investigations may find that the proposed strategies are either impractical, inefficient or do not address the most pressing risks they encounter.
Without a deep understanding of the intricacies of SOC operations, such as the workflows, limitations of existing tools, or the nature of current threat vectors, planners risk designing security strategies or use cases that “miss the mark.” While important, these strategies may focus on hypothetical or emerging threats that do not align with the immediate or most likely risks. Moreover, a lack of input from SOC operators during the planning phase can result in tools, processes, or initiatives that complicate rather than enhance their work, leading to inefficiencies and critical security gaps.
Bridging this gap requires better communication between strategists and operators and a more collaborative approach to security planning. By integrating the practical knowledge and on-the-ground experience of SOC teams with the broader strategic vision, organizations can create more effective, relevant security use cases that address both the current threat landscape and future risks.
Effective communication
Effective communication is critical for the smooth functioning of technical teams, particularly within a SOC, where timely and accurate information exchange can directly impact incident response and overall security posture. SOC teams thrive on precise, actionable, and context-rich communication because they often work in high-stakes environments where decisions must be made quickly and accurately. When leadership or other stakeholders lack an understanding of SOC-specific processes—such as how alerts are triaged, incidents are escalated, or remediation efforts are implemented—it leads to a disconnect. This disconnect can result in a misalignment between the organization’s strategic goals and the SOC’s operational capacity.
Without a clear understanding of the SOC’s workflow, stakeholders might have unrealistic expectations or propose impractical use cases given the SOC’s resources or current threat landscape. For instance, they might expect the SOC to respond to every alert with the same level of urgency, unaware of the nuanced prioritization strategies used by the SOC to prevent alert fatigue. Similarly, they may not recognize the escalation protocols that dictate how and when incidents are handled by different tiers within the team, leading to confusion or frustration when their expectations are unmet.
Bridging this communication gap is essential. Clear, two-way communication helps align strategic initiatives with the SOC’s tactical execution capabilities, ensuring that the work being done is valuable and feasible. Leadership can set more informed priorities, and the SOC can focus on tasks that have a meaningful impact on the organization’s security posture rather than being mired in low-priority or misunderstood tasks.
This kind of communication fosters a collaborative environment where the SOC isn’t just busy responding to alerts. It is engaged in purposeful, impactful work that enhances the organization’s resilience against security threats.
Use Case process triggers
Understanding the factors that can initiate a use case process is critical for streamlining workflows and implementing proactive security measures. By identifying and analyzing these initiating factors, organizations can anticipate potential challenges, allocate resources more effectively, and ensure that processes run smoothly from start to finish. This knowledge allows teams to preemptively address bottlenecks, optimize task management, and reduce inefficiencies that may arise during execution.
Moreover, in terms of security, recognizing the triggers for a use case process is essential for establishing a responsive framework that mitigates risks. Being able to detect early warning signs or conditions that may prompt security vulnerabilities provides a sense of security, enabling swift action and reducing the potential for breaches or disruptions. This comprehensive understanding forms the foundation for building resilient systems that are both agile and secure, enhancing overall operational effectiveness.
There are typically three primary triggers that set this process in motion:
- Cyber Threat Intelligence (CTI) Communique: This involves receiving actionable intelligence from internal or external sources about emerging threats, vulnerabilities, or attack methods. When a CTI communique is received, it may prompt developing or adjusting a use case to detect, prevent, or respond to the newly identified risks. CTI-driven triggers are vital for maintaining up-to-date security defenses against constantly evolving cyber threats.
- Business Requirement: Changes in business operations, regulatory compliance, or strategic objectives can also trigger the use case process. For instance, a new business service or product might require additional security monitoring or risk management procedures. This type of trigger ensures that security measures are aligned with the organization’s evolving needs, maintaining protection while supporting business growth and regulatory adherence.
- Tuning Requirement: Over time, changes in the IT environment or threat landscape may cause existing security controls to generate false positives or become less effective. A tuning requirement trigger indicates the need to fine-tune the parameters of an existing use case to improve accuracy, reduce noise, and enhance overall performance. Regular tuning is essential for optimizing detection capabilities and minimizing unnecessary alerts.
Recognizing these triggers empowers organizations to refine their security strategies proactively, thereby fortifying their defenses against evolving cyber threats. By staying ahead of potential vulnerabilities, businesses can adapt their security posture in real time, aligning their protective measures with current risk landscapes and overarching business objectives. This proactive approach enhances resilience and ensures that security initiatives support strategic goals, leading to a more robust and cohesive operational framework.
Use Case Intake process
All subsequent actions must follow the same standardized workflow once a use case process has been triggered—regardless of what initiated the trigger. This ensures uniformity in handling, response, and resolution across the board, regardless of the nature or origin of the trigger. Consistency is crucial for maintaining operational integrity, especially in a security environment.
Requirement Validation (Use Case Management Team):
This step ensures that the team has a full grasp of what is being asked, avoiding potential misalignments later in the process.
- Do we clearly understand the scope and objectives outlined in the request?
- Has the trigger event been clearly defined, and do we fully comprehend its conditions?
- Are there any ambiguities or assumptions that need clarification with stakeholders?
Data Validation (Use Case Management Team):
This step ensures that the detection mechanisms for the use case are data-driven and feasible, preventing issues during implementation.
- Do we have access to the necessary data points or telemetry to detect the events outlined in the requirements?
- Is the data reliable, timely, and relevant for accurately identifying the trigger?
- Are there any gaps in our data collection that need to be addressed before proceeding?
Action Validation (SOC):
This step ensures that the SOC team is prepared to respond to the use case triggers with clarity and precision, reducing the risk of mishandling incidents.
- Do the SOC analysts and operators understand the response and actions required once the use case is triggered?
- Are the actions predefined and aligned with standard operating procedures (SOPs)?
- Do we need to develop new playbooks or update existing ones to address this use case appropriately?
Priority Validation (Use Case Management Team):
This step ensures that the use case is prioritized accurately, aligning with the overall risk management and operational strategy.
- Do we understand and agree with the priority level assigned to the use case in terms of its importance and urgency?
- Has the priority been assessed in terms of its potential impact on security posture, business operations, and compliance?
- Is there alignment between stakeholders on the priority assigned, ensuring resources and attention are appropriately allocated?
Use Case Build process
Once the Use Case Management team fully understands the requirements and has gathered all the necessary data, they can implement the use case according to its assigned priority. During this phase, it’s crucial to clearly define the roles and responsibilities within the team to ensure an efficient and high-quality process. Specifically, it’s important to distinguish between the members responsible for building or updating the use case and those in charge of testing it. By assigning these tasks to different team members, you can create a natural separation of duties, which helps prevent bias and allows for more objective testing. This division of labor enhances the quality and robustness of the use case, as it benefits from multiple perspectives and specialized focus areas.
Once the technical aspects of the use case have been thoroughly tested and validated, the next step involves sharing the results and documentation with the SOC. The SOC plays a crucial role in this process, as they are the ones who will ultimately monitor and respond to the generated alerts. It’s essential that the SOC is kept informed about any new or updated use cases. At this point, the SOC will review the alert logic and assess whether they fully understand both the alerts generated by the use case and the actions outlined in the accompanying documentation. This review process ensures that the SOC can appropriately respond to any alerts the use case triggers.
Depending on the described actions within the use case, the SOC may initiate additional measures, such as automating specific steps in the response workflow. Automation is valuable for ensuring alerts are handled efficiently within the Key Performance Indicator (KPI) and Key Risk Indicator (KRI) thresholds. By automating repetitive or time-sensitive actions, the SOC can improve response times, minimize manual effort, and ensure consistent handling of alerts, thereby maintaining alignment with organizational risk and performance objectives. This collaboration between the Use Case Management team and the SOC is vital for the seamless deployment and ongoing management of security use cases.
Use Case Test process
After completing the build phase, the documentation and results are formally presented to the individual or team responsible for initiating the use case. This step involves a detailed review of the use case’s technical and functional aspects, ensuring that all requirements and expectations have been met. Any feedback or concerns raised during this discussion are addressed to refine the solution. Once the initiator or stakeholders approve the outcome, the use case is ready for deployment and can be transitioned to the production environment.
It’s important to note that the formal approval process, which involves a detailed review of the use case, is sometimes optional. This is particularly the case when an urgent or emerging threat is involved. In such scenarios, the need for rapid implementation may override the formal approval process, allowing the use case to be deployed quickly to mitigate the risk. However, this fast-tracked approach is typically reserved for time-sensitive situations where delays could result in significant exposure or harm.
Use Case Production phase
Once the use case is transitioned into the production environment, it is crucial to notify not only the SOC, but also other key stakeholders such as the IT Service Desk and the IT Incident Management team. Their roles are integral to the security process, ensuring that these teams are fully aware of the changes and understand their roles in responding to any security incidents. For example, while the SOC is responsible for monitoring, detecting, and executing the initial response based on the predefined actions in the use case, the IT Service Desk must be prepared to handle end-user support or system access issues that may arise as a result of these actions. Similarly, the IT Incident Management team needs to be aligned with the SOC to effectively coordinate, escalate, and resolve incidents, ensuring minimal impact on business operations. Clear communication between these teams is essential for smooth incident handling, ensuring that once the SOC has acted, the follow-up actions are seamlessly carried out by the respective teams according to their defined roles and responsibilities.
Once a use case is transitioned to the production environment, it is crucial to establish a testing and review schedule promptly. This schedule should include specific timelines for when the use case will undergo testing and when it will be reviewed. Given that the IT environment is in a constant state of flux due to activities such as commissioning and decommissioning assets, integrating new technologies, and phasing out outdated systems, periodic testing is essential to verify that the use case remains functional and effective.
Regular testing ensures that any changes in the IT infrastructure do not adversely affect the use case’s performance or reliability. It also helps identify and address potential issues before they impact end users. Additionally, scheduled reviews are necessary to evaluate the use case’s alignment with evolving business requirements and technological advancements. By maintaining a systematic approach to testing and reviewing, organizations can safeguard their use cases’ continuous operational integrity and relevance in a dynamic IT landscape.
It is equally crucial to periodically validate that the underlying threat elements of a use case remain accurate and relevant. Adversaries continually evolve their techniques and tactics, meaning threat landscapes can shift rapidly. As a result, use cases should be reviewed and updated at least annually to ensure they still effectively address current threats. However, depending on the volatility of the threat element in question, more frequent reviews—such as monthly or quarterly—may be necessary to maintain optimal effectiveness.
While the CTI team can initiate the review process for use cases, it is considered best practice for the Use Case Management team to take a proactive approach and engage with the CTI team. This proactive approach empowers the Use Case Management team to ensure that the use cases are regularly validated against the latest threat intelligence, maintaining their relevance and efficacy in the face of evolving adversarial tactics. Regular collaboration between these teams helps ensure that use cases remain robust and aligned with current threat scenarios.
References
https://www.betaalvereniging.nl/wp-content/uploads/FI-ISAC-use-case-framework-verkorte-versie.pdf
Leave a Reply