Setting up an effective and efficient Enterprise Vulnerability Management (EVM) program is critical because it is a foundational element of an organization’s cybersecurity strategy. In today’s rapidly evolving threat landscape, vulnerabilities in systems, applications, and networks are often the primary avenues malicious actors exploit to breach security defenses. Organizations face significant risks without a structured and well-implemented EVM program, including data breaches, financial loss, reputational damage, and compliance failures.
An efficient EVM program goes beyond merely detecting vulnerabilities; it ensures that risks are systematically identified, prioritized, and addressed based on their potential impact on the organization. This proactive approach lets businesses focus on securing the most critical assets first rather than being overwhelmed by a flood of vulnerabilities. Organizations can allocate their resources more strategically by prioritizing vulnerabilities based on risk, ensuring that the vulnerabilities most likely to be exploited are resolved promptly.
A well-designed EVM program also helps organizations comply with industry regulations and standards. Many sectors, including healthcare, finance, and government, have stringent cybersecurity compliance requirements. Failing to address vulnerabilities in a timely manner not only exposes the organization to security risks but can also result in costly penalties or legal liabilities. An EVM program ensures ongoing compliance by continuously monitoring and remediating vulnerabilities that could compromise the security posture.
Furthermore, an efficient program fosters collaboration between various departments within the organization. Vulnerability management is not solely the security team’s responsibility; it requires input from IT, operations, risk management, and even business leadership.
An effective program builds clear communication channels and aligns remediation efforts with business objectives, helping the organization mitigate risks while supporting its overall goals.
Lastly, establishing an efficient EVM program is essential for maintaining trust with customers, partners, and stakeholders. Any security breach can have far-reaching consequences in the age of increased digital interconnectivity. A robust vulnerability management strategy demonstrates that the organization is committed to protecting its data and its clients’ data. This commitment reduces the likelihood of breaches and strengthens the organization’s reputation as a trusted entity in the marketplace.
Eight elements to think about when setting up an effective and efficient Enterprise Vulnerability Management program
Some things to think about when setting up an effective and efficient EVM program are:
- Stop overwhelming the teams with unmanageable data
- Provide the right context around vulnerabilities
- Move towards proactive security
- Apply risk management principles
- Ensure remediation efforts are aligned with patch management
- Right focus
- Effective reporting and communication
- Determine the right patch priority
Each point is discussed below.
1. Overwhelming the Security Team with Unmanageable Data
When you rely heavily on vulnerability and compliance scans, you’re generating an enormous amount of data—often too much for a security team to handle efficiently. These scans can identify thousands, if not millions, of vulnerabilities across various systems. But not all of these vulnerabilities are critical or pose a real risk to the organization. Without proper context, prioritization, and filtering, you’re essentially handing your team an enormous “to-do list” that is both overwhelming and impractical to complete in any reasonable timeframe.
- Problem: Raw scan results are often comprehensive, showing every potential issue but without much regard to the context of the environment. This leads to decision paralysis, where the sheer volume of vulnerabilities makes it hard for the team to focus on what really matters.
- Solution: Implement a risk-based approach where vulnerabilities are categorized by their potential business impact. This prioritization enables teams to focus on the vulnerabilities that pose the greatest threat, rather than being overwhelmed by low-risk issues.
2. Lack of Context Around Vulnerabilities
A vulnerability identified in a scan may not pose a significant risk depending on its context within the environment. For example, a critical vulnerability on an internal system that is isolated from the internet may be less of an immediate priority compared to a medium-severity vulnerability on an externally facing system. If your reporting is based purely on scan results, it misses this critical context, treating all vulnerabilities as equally important.
- Problem: Scans don’t provide the business or operational context necessary for intelligent decision-making. They only tell you that a vulnerability exists, but they don’t help you understand the potential impact or likelihood of exploitation.
- Solution: Augment scan results with asset criticality information, threat intelligence, and environmental context. Knowing how important a system is to your business operations and whether a vulnerability is actively being exploited in the wild allows you to make smarter decisions.
3. Creating Reactive Rather than Proactive Security
Basing your entire vulnerability management strategy on scan results puts your team in a reactive mode. They are constantly firefighting—responding to vulnerabilities only after they are detected by scans. This approach is unsustainable in the long run and fails to protect the organization against emerging threats that might not be detected by routine scans.
- Problem: A scan-only approach treats security as an after-the-fact process, where vulnerabilities are only addressed once they have already been discovered. This is highly reactive and leaves the organization vulnerable to new threats.
- Solution: Shift towards a more proactive strategy by integrating real-time threat intelligence, continuous monitoring, and patch management. This allows your team to address vulnerabilities before they become critical issues, rather than scrambling to fix them afterward.
4. Neglecting Risk Management Principles
Enterprise Vulnerability Management should be about managing and reducing risk, not simply patching every vulnerability that a scan identifies. When your program is entirely scan-driven, you lose sight of the broader goal: protecting the organization from the most significant threats. Treating every vulnerability as an equal priority results in wasted resources, as time is spent remediating low-risk issues while more significant threats may go unaddressed.
- Problem: Scan-driven reporting often focuses on quantity over quality—how many vulnerabilities were found and fixed—without any insight into whether the organization’s overall risk posture has improved.
- Solution: Adopt a risk-based approach where vulnerabilities are prioritized based on their potential impact on the business. This involves considering factors like the criticality of affected systems, the likelihood of exploitation, and the severity of the vulnerability. Addressing the most significant risks first helps ensure that remediation efforts are aligned with the organization’s broader risk management strategy.
5. Inadequate Remediation and Patch Management
The end goal of vulnerability management is not just identifying issues but remediating them effectively. However, if your reporting is based solely on scan results, it’s easy to get bogged down in the identification phase and lose sight of remediation efforts. Large lists of vulnerabilities can overwhelm IT and security teams, making it difficult to track which vulnerabilities have been addressed and which are still outstanding.
- Problem: If scans continuously produce large volumes of vulnerabilities without a streamlined process for remediation, vulnerabilities can remain unpatched for long periods, increasing the organization’s exposure to risk.
- Solution: Establish automated workflows that integrate vulnerability scans with IT service management tools to streamline remediation efforts. Assign vulnerabilities to appropriate teams, track progress, and ensure that patches are applied in a timely manner. This ensures that vulnerabilities don’t sit unpatched simply because the team is overwhelmed by the sheer number of issues.
6. Focusing on Compliance Instead of Security
Compliance scans are necessary for regulatory requirements, but they should not be the sole focus of your vulnerability management program. Compliance standards often define a minimum baseline of security and are not necessarily aligned with current threat landscapes. By focusing too heavily on compliance scans, organizations can end up addressing vulnerabilities that matter from a regulatory perspective but overlook those that pose more immediate security risks.
- Problem: Compliance-driven programs often result in security teams focusing on passing audits rather than reducing actual risk to the business. This can create a false sense of security, where vulnerabilities that don’t fall under compliance requirements are ignored.
- Solution: Use compliance as one aspect of your program, but not the entire focus. Ensure that your vulnerability management strategy addresses real-world threats and risks, going beyond what’s required for compliance to create a truly secure environment.
7. Ineffective Reporting and Communication
Reports generated from scan results are often large and difficult to interpret, particularly for non-technical stakeholders. This results in a disconnect between technical teams and business leaders. Without clear, actionable reporting, it’s difficult for executives to understand where the organization’s true risks lie and whether the vulnerability management program is achieving its goals.
- Problem: Reports based purely on scan results lack context and clarity, making it difficult for decision-makers to understand the state of security. These reports tend to focus on metrics like the number of vulnerabilities found or patched, which don’t necessarily reflect the organization’s overall risk posture.
- Solution: Develop more meaningful, risk-based reports that translate technical vulnerabilities into business risks. This enables executives and stakeholders to make informed decisions about resource allocation and prioritization.
8. Determine the right patch priority
Using the CVSS (Common Vulnerability Scoring System) standard to prioritize remediation efforts is essential for effective vulnerability management. However, simply relying on the base CVSS score, which measures a vulnerability’s intrinsic properties, can often be insufficient. To create a more accurate and actionable prioritization, it is crucial to consider two additional CVSS metrics: environmental and temporal metrics. These provide valuable context, enabling teams to focus on vulnerabilities that pose the greatest real-world risk to their specific environment.
The environmental metric tailors the CVSS score based on the unique characteristics of an organization’s infrastructure, such as the criticality of assets and how exposed they are within the network. The temporal metric incorporates real-time threat data, such as whether the vulnerability is actively exploited in the wild or whether a known fix is available. These metrics allow organizations to move beyond a one-size-fits-all approach to vulnerability management, focusing on the vulnerabilities that pose the most immediate risk.
However, embedding these metrics into the remediation process can be challenging. Unlike base metrics readily available from vulnerability databases, environmental and temporal metrics require input from various internal systems. For example:
- Configuration Management Database: Provides critical information on the assets affected by the vulnerability, including the business impact and priority of each asset.
- Network Diagrams: Help to understand how the vulnerable systems are connected and whether they are exposed to potential attack vectors, such as being accessible from the internet.
- Cyber Threat Intelligence Platforms: Supply up-to-date information on whether the vulnerability is actively being exploited, helping to assess the urgency of remediation.
Integrating all of this data into the vulnerability management process is complex. It requires collaboration between multiple teams, such as security, IT, and network engineers, and a seamless flow of information across systems. Additionally, each system must be updated, ensuring that any changes in asset configurations, network architecture, or threat landscape are reflected in the vulnerability prioritization process.
This complexity often makes integrating environmental and temporal metrics a “slight nightmare.” It demands robust automation, cross-team communication, and advanced tools to pull data from disparate sources and correlate it effectively. However, despite these challenges, embedding these metrics into the remediation process is critical for ensuring that the organization focuses on the most critical and exploitable vulnerabilities, enhancing overall security posture.
Threat Metric
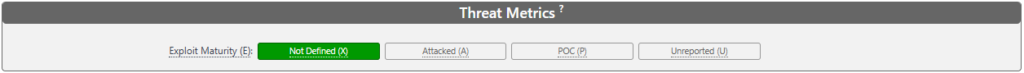
The Cyber Threat Intelligence (CTI) team plays a crucial role in enhancing vulnerability management by providing real-time insights into which vulnerabilities are actively being targeted by adversaries. Their input is particularly valuable when it comes to refining the CVSS (Common Vulnerability Scoring System) score, specifically through the temporal metric. This metric adjusts the base CVSS score based on real-world conditions, such as the availability and maturity of exploit code, which can dramatically influence the prioritization of remediation efforts.
One of the key factors the CTI team can help assess is whether a working exploit exists for a given vulnerability. By default, the CVSS assumes that a functional exploit is available, which typically drives up the severity of the score. However, if the CTI team determines that no exploit code is publicly available or only a proof-of-concept (PoC) version exists, the vulnerability may be less of an immediate threat, and the score can be adjusted accordingly.
- No exploit code available (-0.9 point): If there is no known exploit code available, it significantly lowers the urgency of the vulnerability. The absence of a reliable exploit indicates that the likelihood of immediate exploitation is reduced, leading to a decrease in the CVSS score by approximately 0.9 points. This adjustment allows security teams to deprioritize vulnerabilities that, while potentially serious, are less likely to be exploited in the near term.
- Proof-of-Concept (PoC) exploit code (-0.7 point): In cases where only a PoC exploit is available, the risk is lower than with a fully developed exploit but still present. A PoC demonstrates that the vulnerability can be exploited in a controlled environment, but it might not yet be reliable or widely usable in the wild. This reduces the CVSS score by around 0.7 points, reflecting that while exploitation is possible, it may not be imminent or easily achievable by adversaries.
Environmental Metric
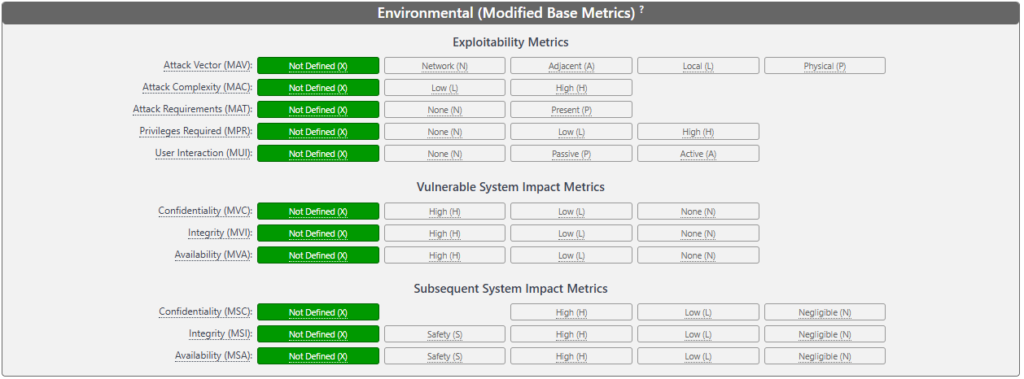
The Attack Vector (AV) metric in the CVSS standard is indeed crucial for understanding where a potential exploit could originate. In the case of a “flat” network—where there is little or no segmentation—it’s relatively straightforward to assess the attack vector, as an adversary has unrestricted lateral movement within the network. However, modern networks are increasingly segregated, meaning that different network zones (such as production, development, or DMZ) are separated to limit the pathways available for an attacker. This segregation complicates the determination of the attack vector because it’s no longer simply a question of where the vulnerability exists, but where an attacker could reasonably initiate an attack.
In a highly segregated network, the attack vector can vary depending on the access controls and network segmentation in place. For example, when the CVSS base attack vector (AV) is listed as N (Network), meaning that the vulnerability could be exploited from a remote network location, in reality, due to the network segmentation, the Modified Attack Vector (MAV) could be A (Adjacent)—indicating that the exploit can only be initiated from within a neighboring or connected segment. This results in a reduction of the CVSS score by approximately 0.6 points, reflecting the reduced likelihood of exploitation due to the restricted attack surface.
Leave a Reply