By adhering strictly to the Purdue model, your OT environment will exclusively consist of essential devices required for seamless factory operations, effectively mitigating IT-related threats. However, as is often the case, theory and practice diverge. In reality, the situation is more intricate. Let’s delve into the myriad facets of this issue to help you determine the optimal approach for your environment.
The initial hurdle in implementing the Purdue model lies in Identity and Access Management (IAM). This is a critical consideration, and it immediately raises a challenging question: “Central authentication or decentralized authentication?” Each option comes with its own set of advantages and drawbacks, necessitating a careful evaluation.
Opting for central authentication may seem convenient, as it simplifies access control by utilizing a single, authoritative source. However, this convenience comes at a cost, primarily in the form of increased exposure to IT-related threats within the OT-environment. While you can isolate central authentication within a dedicated domain accessible only from the OT-environment, there’s a significant vulnerability inherent to this approach. If the central authentication system is compromised, it grants adversaries access to every device relying on central authentication. This concentrated risk can have severe consequences for your OT operations.
On the other hand, decentralized authentication may appear to mitigate these risks by distributing authentication responsibilities across various devices or assets. However, it’s essential to scrutinize this choice from a cybersecurity standpoint. Some argue that decentralized authentication may not significantly differ from central authentication in terms of vulnerability. In fact, it can potentially exacerbate the situation by increasing the attack surface, making it more challenging to implement effective authentication-related use cases within the Security Operations Center.
In essence, the choice between central and decentralized authentication is a complex one, with trade-offs in terms of convenience, security, and manageability. Finding the right balance that aligns with your specific OT-environment’s needs and risk tolerance is crucial. Thorough risk assessment, continuous monitoring, and proactive security measures are essential components of a successful IAM strategy in the context of the Purdue model.
Exploring the next crucial aspect, we encounter the complex realm of vulnerability management within your OT environment. In theory, it might appear straightforward: conduct discovery, vulnerability assessment, and compliance scanning within your OT landscape to pinpoint weaknesses. However, the reality is far more intricate.
The challenge stems from the fact that Programmable Logic Controllers (PLCs) and Supervisory Control and Data Acquisition (SCADA) devices were conceived in an era when vulnerability scanning was not a consideration. Consequently, they often struggle to gracefully accommodate vulnerability scans. To circumvent this, there are passive vulnerability scanning solutions available. But even with this approach, there remain intricate questions to address.
Firstly, does your OT environment boast a clear demarcation between PLC/SCADA devices and other components? Achieving such separation can be an onerous task. Furthermore, even if this separation exists, organizational policies may govern when and how vulnerability scans are performed. These policies could limit scanning to only overloaded maintenance windows, constraining the frequency and scope of vulnerability assessments.
However, it’s crucial to underline the immense value that vulnerability scanning brings to your Security Operations Center. Beyond driving remediation efforts, vulnerability data plays a pivotal role during incident response and triage. It aids in painting a clearer picture when evaluating whether a generated alert is a true positive or a false positive. In essence, comprehensive vulnerability management not only strengthens your security posture but also empowers your organization to respond more effectively to potential threats within the intricate landscape of your OT environment.
In a typical OT environment, you may encounter operating systems that are not too dissimilar from those commonly found in traditional IT environments. Examples include Microsoft Windows and Linux, which, despite their presence in the OT world, remain susceptible to malware and ransomware — quintessential IT cyberthreats. One might assume that the solution lies in installing enterprise anti-malware and Endpoint Detection and Response (EDR) systems, but it’s not always that straightforward.
Firstly, not every OT equipment supplier grants the freedom to install enterprise-level anti-malware and EDR solutions. Their apprehension often stems from concerns that such software could disrupt the functionality of the equipment, potentially leading to issues with the agreed Service Level Agreements (SLAs). This constraint makes it necessary to navigate a delicate balance between securing the OT environment and maintaining the uninterrupted operation of critical equipment.
Secondly, the OT environment presents another unique challenge — the prevalence of outdated operating systems. Unlike their IT counterparts, where devices are typically replaced every 4 to 6 years, OT environments often adhere to much longer lifecycle management programs, stretching up to 20 years. This extended lifespan amplifies the risk associated with operating systems that may no longer receive regular security updates and patches, rendering them more susceptible to cyber threats.
Consequently, safeguarding an OT environment demands a more nuanced approach, involving a thorough assessment of the compatibility of security solutions with existing equipment, strategic planning to address longer lifecycle spans, and a meticulous consideration of the potential impact on operational continuity. Balancing the imperative to secure these critical systems with the constraints of the OT landscape requires a bespoke strategy that goes beyond a one-size-fits-all IT security model.
Prolonged equipment life-cycles in the industrial setting introduce a unique set of challenges. One of the significant hurdles stems from the fact that vulnerabilities in these systems can linger undiscovered for extended periods before they are effectively addressed. If you’ve adopted the Purdue model and solely rely on VLANs and routers to segregate your assets and manage risks, you might not adequately tackle the risk aspect of your environment.
Implementing an appropriate firewall architecture, on the other hand, can substantially reduce the chances of a vulnerability being exploited. Moreover, in the event that a vulnerability is exploited, a well-designed firewall system can contain the damage, limiting what’s known as the “blast radius” or the potential scope of harm. The beauty of creating such a firewall architecture in the context of most OT solutions is that, while it is labor-intensive, the design process itself is relatively straightforward.
In a typical OT solution, the communication flow follows a distinct pattern: the PLC communicates serially with a SCADA controller, and the SCADA controller communicates with a Human-Machine Interface (HMI) via TCP/IP in a point-to-point fashion. To enhance security, you can impose restrictions by limiting the size of the VLAN and narrowing down communication flows to the absolute minimum necessary. This not only reduces the potential damage radius but, more critically, any deviations from established communication patterns can serve as red flags, signaling a potential security incident.
However, it’s essential to note that effectively implementing such a firewall architecture requires a dedicated OT-SOC. This is due to the fact that a deep understanding of OT systems is imperative to make informed decisions and effectively respond to security incidents in this unique environment. Consequently, this approach demands a substantial investment in expertise and resources to fortify the security posture of your OT infrastructure.
One crucial consideration when determining whether to establish a dedicated OT-SOC revolves around incident response. While, at a high level, the NIST incident response model remains consistent across both IT and OT environments, the practical execution differs significantly. This distinction primarily stems from the potentially monumental consequences of actions taken in the OT sphere.
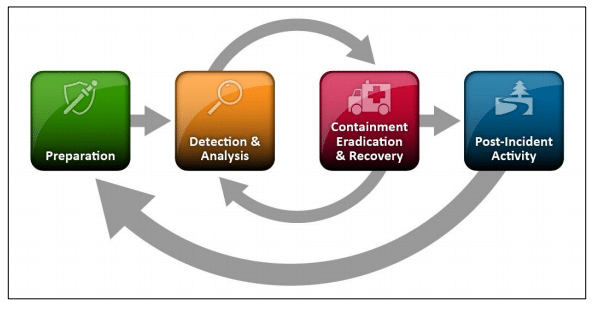
In a traditional IT environment, when facing a malware outbreak, a common response is to isolate and contain the affected device. However, implementing the same approach within an OT environment carries substantial risks. The reason lies in the substantial impact that OT disruptions can have. Imagine a scenario where you isolate a device on an OT network in a factory. This action, seemingly innocuous in an IT context, could inadvertently disrupt the entire factory production line, potentially leading to disastrous consequences, even endangering lives.
Herein lies the pivotal advantage of having a dedicated OT-SOC. Such a specialized facility is better equipped to design and execute precise incident response strategies tailored to the unique challenges of OT. They possess the expertise to navigate intricate OT incident scenarios without compromising the core functions of critical systems. This nuanced understanding and capability make a dedicated OT-SOC a prudent choice for safeguarding your OT environment, as opposed to relying solely on a more general IT-SOC.
Depending on how your organizational structure is set up, establishing a dedicated OT-SOC doesn’t necessarily imply duplicating the SIEM and SOAR platforms. In fact, having a shared SIEM and SOAR platform is a viable option, provided it’s strategically positioned within your enterprise architecture. When you opt for a shared approach, it’s crucial that these platforms are located in a DMZ situated between the IT and OT environments. Access to these platforms should only be permitted through a proxy or stepping solution.
This architectural arrangement serves a dual purpose. First, it safeguards the SIEM and SOAR platforms themselves, creating an additional layer of defense. Second, it restricts the potential for these platforms to be exploited as a stepping stone for cyber threats to traverse from the IT environment into the OT environment.
One of the prominent advantages of employing a shared SIEM platform is its capacity to correlate security alerts across the entire environment. This capability allows for a more comprehensive understanding of potential threats and facilitates a quicker and more effective response. However, it’s important to note that if your company’s risk tolerance doesn’t permit shared access, similar results can be achieved by implementing well-defined processes and interlocks between the IT and OT security teams. These measures can enable effective information sharing and coordination without the need for a shared SIEM platform, ensuring that security remains robust while aligning with your risk management policies.
Evaluating the need for a dedicated SOC in the context of your OT environment is a nuanced and complex undertaking. It requires a comprehensive analysis that delves into multiple facets, some of which are briefly addressed in this article, though not all-inclusive. The heart of this matter converges on a fundamental inquiry: “What level of risk is your company willing to accept?” Your answer to this critical question serves as the compass, steering your determination regarding the necessity of a dedicated OT-SOC.
The decision to establish a dedicated OT-SOC hinges on your organization’s unique risk appetite, which encompasses a range of considerations. These may encompass the criticality of your OT systems, the potential impact of security breaches, regulatory compliance requirements, and the ever-evolving threat landscape. Moreover, it entails an in-depth evaluation of your existing cybersecurity capabilities, including incident detection, response capabilities, and the capacity to safeguard sensitive OT assets.
Ultimately, as you navigate this intricate terrain, your risk tolerance and the specific demands of your OT infrastructure will be the guiding factors in determining whether a dedicated SOC is not only beneficial but indeed an indispensable component for ensuring the security and resilience of your OT-environment.
Leave a Reply