Artificial Intelligence, commonly referred to as AI, has undeniably become the prevailing marketing buzzword in recent times. The excitement surrounding AI is palpable, and it has captured the imagination of industries and individuals alike. However, the crucial question is whether AI can truly live up to these soaring expectations. In my view, the answer is a cautious one; the current state of AI, though promising, still carries certain limitations due to its emerging and relatively immature nature.
While AI has indeed made significant strides, particularly in areas like machine learning, natural language processing, and computer vision, it remains a technology in its evolutionary phase. Its potential is vast, and it has shown impressive results in automating tasks, data analysis, and decision-making processes. Yet, its capabilities are not universally comprehensive, and it often requires human intervention or guidance to navigate complex and nuanced scenarios.
AI’s immaturity is evident in its inability to replicate human-like common sense reasoning, adapt to rapidly changing situations, or possess a deep understanding of context. The challenge of ensuring the ethical and responsible use of AI is also a pressing concern. Bias in AI algorithms, data privacy issues, and security vulnerabilities are just a few examples of the challenges that need to be addressed for AI to be considered mature.
However, it is vital to recognize that AI’s immaturity does not equate to worthlessness. AI systems can provide significant value across various domains when deployed thoughtfully. It can streamline processes, provide valuable insights from large datasets, and contribute to solving complex problems. As AI technology continues to advance, it has the potential to transform industries, drive innovation, and improve our daily lives.
AI, as described by Britannica, is the remarkable capacity of a digital computer or a computer-controlled robot to execute tasks that are typically linked with intelligent beings. Nevertheless, the key challenge embedded in this definition is the concept of “intelligence” itself. How do we truly define intelligence, and how can we assess it effectively?
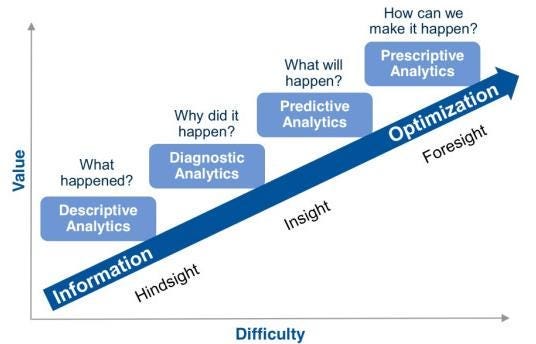
To define intelligence, one can look at it as the ability of a system to engage in a spectrum of cognitive functions, including descriptive, diagnostic, predictive, and prescriptive analytics, ideally within a concise timeframe. In this context, intelligence transcends mere data processing and involves a deeper understanding and application of information.
In the realm of AI, these analytics categories serve as benchmarks for measuring the depth of a system’s intelligence. Here’s how they apply to a typical monitoring use case:
- Descriptive Analytics: A monitoring use case primarily operates within the domain of descriptive analytics. It involves tracking and observing various data sources in real-time, seeking to identify patterns, anomalies, or deviations from established norms. If it aligns with predefined monitoring rules, it can quickly pinpoint potential threats or issues.
- Diagnostic Analytics: While most of the work in a monitoring use case pertains to descriptive analytics, it moves slightly toward diagnostic analytics when an alert is raised. When an alert is triggered, it doesn’t merely identify an anomaly but also delves into why it occurred. This phase involves the analysis of the raised alert, aiming to understand the root causes or triggers of the issue.
- Predictive Analytics: Going beyond diagnostics, predictive analytics entails forecasting future events based on historical data and patterns. An intelligent system should be able to use the insights gained from diagnostic analytics to predict potential future threats or issues. This capability enhances proactive decision-making and risk mitigation.
- Prescriptive Analytics: The highest level of analytical intelligence is prescriptive analytics. It involves not only predicting future events but also recommending actions to mitigate or capitalize on them. An AI system demonstrating prescriptive capabilities can offer guidance on how to address issues, potentially automating responses to certain situations.
Therefore, intelligence, in the context of AI, is a multifaceted construct that spans a continuum from basic data observation (descriptive analytics) to in-depth problem-solving (diagnostic analytics), forward-looking predictions (predictive analytics), and even autonomous decision-making (prescriptive analytics). The measure of an AI system’s intelligence lies in its ability to traverse this spectrum effectively and efficiently, providing valuable insights and actionable guidance to its human counterparts, as well as facilitating more informed and proactive decision-making.
In the ever-evolving realm of data science, we find ourselves amidst a transformative era where predictive models take center stage, playing a pivotal role in determining the authenticity of raised alerts. This is especially pronounced in the context of security and incident response, where these models act as indispensable tools, guiding us in discerning the demarcation between a “true-positive” alarm and a “false-positive” one. The significance of this task cannot be overstated, as it wields far-reaching implications for the safety, reliability, and operational efficiency of myriad systems and processes.
At the core of these alert prediction models lies a sophisticated web of historical data. They diligently sift through the annals of past incidents and their associated alerts, drawing from this rich tapestry of information to make astute and informed assumptions about the nature of new alerts. This foundational premise rests on the idea that by harnessing the underlying patterns and distinct characteristics of previously validated alerts, one can accurately forecast the veracity of the present alert. Yet, even as these models demonstrate their mettle, they unfailingly raise two vital questions that command our attention when we place our trust in them.
First and foremost, we must grapple with the issue of model accuracy and reliability. How well can we truly trust these predictive systems to differentiate between real security threats and mere false alarms? The effectiveness of these models hinges on their capacity to capture the intricacies of evolving threats and the dynamic nature of security landscapes. Thus, ongoing validation and fine-tuning are essential to ensure that these models remain attuned to the ever-shifting patterns of malicious activity.
Secondly, we must navigate the ethical terrain of predictive models in security and incident response. The power vested in these algorithms to classify alerts carries substantial consequences. Their judgments can result in the mobilization of resources, incident responses, and even legal actions. Thus, there is a pressing need to address concerns related to potential biases, fairness, and the ramifications of false negatives, where genuine threats are mistakenly dismissed. These models demand a careful balance between automation and human oversight to mitigate potential risks and ensure that their deployment adheres to ethical principles.
The importance of these inquiries becomes all the more evident when we grasp the profound impact that the outcomes of predictive models have on the operation of a SOAR platform. SOAR platforms serve as the bedrock of modern cybersecurity, orchestrating and automating incident response protocols according to the intelligence they glean from incoming data. In essence, they serve as the vigilant sentinels of digital security, ready to respond swiftly to emerging threats.
In this context, the integrity and reliability of the predictive models become paramount. The accuracy and timeliness of these models are the lynchpins upon which the effectiveness of a SOAR platform hinges. If the predictive models are flawed, outdated, or otherwise unreliable, the consequences can be profound and far-reaching. This is where the gravitas of the situation unfolds.
Inaccurate or obsolete predictive models can lead a SOAR platform to undertake actions that are either unwarranted or ineffectual in the face of a cybersecurity incident. This not only squanders precious resources and time but may also inadvertently exacerbate the situation. For instance, an errant prediction might trigger an unnecessary lockdown of systems, causing operational disruptions and unnecessary alarm, or it may fail to detect a genuine threat, allowing it to proliferate unchecked. In both cases, the consequences are undesirable and potentially disastrous.
Therefore, it is imperative that organizations invest in maintaining, updating, and refining their predictive models to ensure the SOAR platform’s actions are aligned with the ever-evolving threat landscape. The precision and reliability of these models are the linchpins that determine whether a SOAR platform operates as a shield against cyber threats or inadvertently becomes a catalyst for chaos in the complex world of cybersecurity. The integrity of these predictive models is, in essence, the cornerstone of proactive and effective cybersecurity.
In the broader context of security and automation, the convergence of predictive models and SOAR platforms exemplifies a crucial equilibrium that organizations must establish. This equilibrium requires a meticulous assessment of two pivotal factors: the precision of predictive models and the currency of data updates. By carefully managing these aspects, organizations can guarantee that their automated security responses are not only streamlined but also highly productive.
Predictive models serve as the bedrock of this security and automation synergy. These models leverage historical data, machine learning algorithms, and a wealth of information to anticipate potential security threats or vulnerabilities. They play a pivotal role in identifying emerging risks, anomalies, or patterns that might be indicative of a security incident. However, the reliability and precision of these predictive models are paramount. Organizations must continually refine and validate their models to ensure they remain accurate in the ever-evolving threat landscape.
Equally important is the timely and consistent updating of data. Security events unfold rapidly, and an outdated dataset can significantly impede the effectiveness of automated security responses. If the data is not current, the predictions made by the models might not align with the real-world situation, potentially resulting in false positives or missed threats. Therefore, organizations must implement robust data collection and processing procedures, as well as employ mechanisms to refresh this data in real-time or near real-time, to keep the predictive models well-informed.
The delicate balance lies in harmonizing these two elements — the accuracy of predictive models and the timeliness of data updates. On one hand, overreliance on predictive models without due consideration of their precision may lead to erroneous automated responses that disrupt operations and erode trust. On the other hand, disregarding the timeliness of data updates can render these models obsolete, rendering the automation ineffective when it is needed most.
Neglecting the need to effectively tackle these concerns can set the stage for a series of unfortunate events, akin to the noteworthy challenges encountered by the Microsoft chatbot. This chatbot, at one point, made headlines for all the wrong reasons as it generated responses that stirred controversy and public outrage. This unfortunate episode serves as a stark reminder of the perilous path one walks when deploying automated systems without a vigilant eye on quality control and continuous model maintenance.
However, it’s crucial to understand that these concerns extend beyond mere public relations issues. They take on a far more ominous dimension when we venture into the realm of security. In the context of security, the stakes are exponentially higher, as the consequences of algorithmic failures can reverberate across an entire organization and its stakeholders, leaving a trail of chaos in their wake.
When we speak of errors in the security domain, we aren’t merely discussing potential PR nightmares; we are delving into the very heart of an organization’s safety and the integrity of its critical systems and sensitive data. An automated system’s failure to function as intended or its susceptibility to exploitation could lead to catastrophic breaches, jeopardizing the confidentiality, availability, and integrity of invaluable information. This, in turn, poses a real and immediate threat to not only an organization’s reputation but, more importantly, to the safety and well-being of individuals whose data may be at risk.
Technology companies frequently tout their capacity to identify and analyze anomalies in user and device behavior, a domain commonly known as UEBA. While these claims may sound remarkable, it is crucial to scrutinize them more closely. To gain a genuine understanding of human behavior, one often needs to possess a background in psychology — a crucial aspect that is regrettably overlooked in the glossy marketing materials of technology vendors.
At first glance, the promise of UEBA seems groundbreaking. It suggests the ability to detect deviations from established behavior patterns, uncovering potential security threats, fraud, or other abnormal activities. However, the reality is more intricate than these initial assertions. UEBA systems rely on algorithms, data analysis, and machine learning to identify anomalies. While these technologies are undeniably powerful, they lack the nuanced understanding of human behavior that a psychologist can provide.
Human behavior is a multifaceted and intricate subject that goes far beyond mere data points and patterns. It encompasses emotional, cognitive, and even cultural factors that significantly influence how individuals interact with technology. A psychology background enables a professional to fathom the motivations, emotions, and social dynamics that drive human actions. It allows them to interpret behavior in a more holistic manner, considering the why, not just the what.
Moreover, a psychological perspective acknowledges that individuals’ behaviors evolve and adapt over time, which may appear as anomalies to a rigid algorithm. For example, a sudden increase in late-night online activity might be flagged as an anomaly by a technology system, but a psychologist could recognize it as a shift in the user’s personal habits due to a new job or life event.
Incorporating psychology into UEBA can enhance the effectiveness and accuracy of anomaly detection. This approach recognizes that while technology is a powerful tool, it should work in conjunction with the human element to truly comprehend and predict behavior. Technology vendors should acknowledge the importance of this multidisciplinary approach and not oversimplify the complexities of human behavior when making their claims.
The challenge associated with User and Entity Behavior Analytics (UEBA) extends far beyond the absence of psychological expertise in its development; it delves into the very essence of how these systems are designed and trained. Many UEBA models embrace a continuous learning approach, which enables them to adapt to evolving behaviors in real-time. While this adaptability may initially appear to be a strength, it paradoxically exposes a critical vulnerability.
This vulnerability stems from the fact that malicious actors are acutely aware of how UEBA systems operate and leverage this understanding to their advantage. They can employ a sophisticated strategy by gradually and subtly altering user or device behavior patterns, all with the explicit intention of evading detection. These nuanced changes may occur at a pace that outstrips the UEBA’s ability to establish a solid baseline of normal behavior.
Where UEBA excels is in identifying sudden deviations from the established behavioral models. However, it’s crucial to remember that these models fall under the category of descriptive analytics. They provide a retrospective view of behavior. Therefore, human verification remains essential. For instance, an employee may initiate a new project, causing temporary deviations in the trained models. Without human intervention and understanding, these deviations might be misinterpreted as malicious activities.
Transitioning from descriptive analytics to more advanced stages is a formidable challenge, requiring a significant shift in analytical capabilities. The initial roadblock to conquer in this journey is the realm of diagnostic analytics, and it’s a substantial one. Diagnostic analytics demands the development of models with the cognitive capacity to comprehend and discern both human and device behaviors within the data.
A crucial element of effective incident response is containment, which serves as the initial line of defense in mitigating and rectifying security breaches. To excel in incident containment, a profound understanding of the incident itself is paramount. It’s not sufficient to merely observe what is unfolding; the key is to grasp why these events are transpiring. Only when you’ve delved into the ‘why’ behind an incident can you genuinely hope to effectively contain it.
Once you’ve surmounted the diagnostic analytics challenge, the transition to predictive analytics becomes relatively more manageable. Diagnostic analytics lays the foundation by creating models that can detect and profile the behaviors of potential threat actors. With the knowledge garnered from diagnostic analytics, predictive analytics empowers you to conduct simulations and scenario analysis, envisioning the various pathways a threat actor might take within your system or environment.
It is crucial not to rush into purchasing simulation products without careful consideration. Your organization should possess a well-established and mature IT and Security posture before venturing into this realm. Failing to do so can result in a considerable waste of both time and effort.
Prescriptive analytics, a more advanced stage of data analysis, becomes relevant only after predictive analytics has been successfully implemented. It revolves around a fundamental question, “How can we effectively prevent malicious actors from infiltrating our environment?” This question lies at the heart of an Enterprise security architect’s responsibilities and is undeniably one of the most critical tasks in safeguarding an organization’s assets.
Embarking on the path to successfully integrate data science into security practices necessitates a meticulous and systematic approach. The initial step in this journey involves conducting a thorough and holistic examination of your current SOC. To facilitate this evaluation, the Capability Maturity Model Integration (CMMI) framework emerges as an invaluable tool.
The CMMI model is a structured and well-established framework renowned for its efficacy in gauging and augmenting the maturity levels of diverse organizational processes. This model, widely recognized and employed across various industries, extends its applicability to the realm of security.
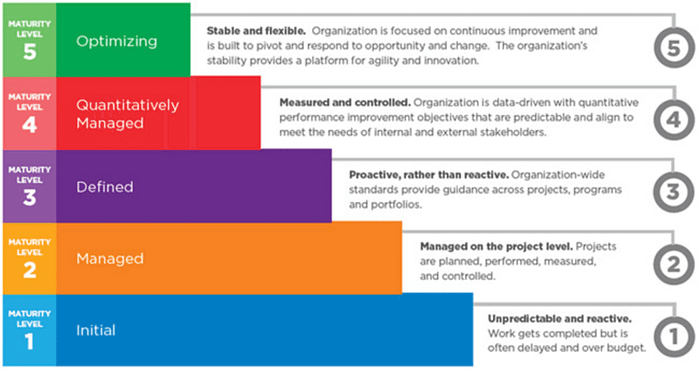
In essence, the CMMI model serves as a guiding light in the journey towards data-driven security enhancement. It furnishes a structured and well-defined set of standards and best practices to assess and elevate the maturity of your security processes. This approach entails a step-by-step progression from initial, often ad-hoc security procedures to a well-defined and optimized state, ultimately leading to more robust and effective security measures.
By leveraging the CMMI framework, you’ll be able to conduct a comprehensive appraisal of your existing security practices. This evaluation encompasses a wide array of elements, including the proficiency of your personnel, the effectiveness of your tools and technologies, the coherence of your processes, and the alignment of your security strategy with broader organizational goals.
Furthermore, the CMMI model provides a roadmap for gradual improvement, allowing you to address weaknesses in your security posture incrementally. This step-by-step approach not only ensures a smoother transition towards data science integration but also facilitates the creation of a strong foundation for advanced security analytics and threat detection. Ultimately, the implementation of data science in security can be more seamless and effective when built upon a solid foundation of well-assessed and enhanced security processes, thanks to the guiding principles of the CMMI framework.
Here’s an enhanced and elaborated explanation of how CMMI can assist in this process:
- Structured Assessment: CMMI provides a structured and systematic approach to assessing the maturity of your security organization. It offers a set of standardized criteria and best practices that help you evaluate your security processes objectively. This structured approach ensures that you cover all critical areas of security, leaving no room for oversight.
- Continuous Improvement: CMMI emphasizes a culture of continuous improvement. By applying CMMI to your security organization, you can identify areas where you can enhance your security processes and practices. This iterative approach allows you to adapt to evolving threats and security challenges effectively.
- Benchmarking: CMMI enables you to benchmark your security organization against industry standards and best practices. This comparison helps you understand where your security maturity stands relative to your peers and competitors. It also allows you to set realistic goals for improvement.
- Risk Mitigation: As you assess your security organization’s maturity using CMMI, you can pinpoint vulnerabilities and weaknesses in your processes. This, in turn, enables you to prioritize and address the most critical security risks. By mitigating these risks, you enhance your overall security posture.
- Resource Allocation: CMMI can help you allocate resources more efficiently. It assists in identifying areas where investments in people, technology, or processes are most needed. This ensures that your resources are used strategically to improve your security capabilities.
- Standardization: One of the key strengths of CMMI is its focus on standardization. By standardizing your security processes, you create a consistent and repeatable framework for managing security across your organization. This reduces the likelihood of human error and enhances the overall security culture.
- Management Support: CMMI can garner support from top management for security initiatives. When you can demonstrate the maturity of your security organization using a recognized framework like CMMI, it becomes easier to secure the necessary budget and support from executives and stakeholders.
- Documentation and Accountability: CMMI encourages thorough documentation of security practices and processes. This not only provides a valuable resource for future reference but also enhances accountability within the organization. When responsibilities are clearly defined and documented, it’s easier to ensure that security measures are consistently followed.
- Scalability: CMMI is adaptable to organizations of various sizes and complexities. Whether you’re a small startup or a large enterprise, the framework can be tailored to suit your specific needs. This scalability makes it a valuable tool for measuring security maturity in a wide range of settings.
- Competitive Advantage: A mature security organization can become a competitive advantage. By using CMMI to measure and enhance your security maturity, you can demonstrate to customers, partners, and regulators that you take security seriously, potentially setting your organization apart in the marketplace.
Embarking on a successful journey in the dynamic realm of data science requires a dedicated pursuit of proficiency, ideally reaching a benchmark level of four or higher. This threshold represents a pivotal milestone, serving as the bedrock criterion that underscores your readiness to dive into the intricacies of data science. It is, in essence, a litmus test of your abilities, indicating your capacity to not only navigate but also thrive in this multifaceted field.
Achieving a proficiency level of four or higher is more than just a mere aspiration; it is the bridge that connects your theoretical foundation with practical proficiency. It is the point at which your skills and knowledge converge, equipping you with the competencies essential to extract valuable insights from data, develop predictive models, and make informed decisions.
To reach this benchmark level, one must delve into the realms of statistics, machine learning, programming, and domain-specific knowledge, among other facets. It is a multifaceted journey, encompassing the art of data wrangling, the science of data analysis, and the craft of data visualization. Moreover, it demands a keen understanding of the ethical considerations and practical challenges that come with handling and interpreting data.
Once this level of proficiency is attained, you are poised to contribute significantly to the field of data science. You become an asset, capable of unraveling complex data puzzles, providing actionable insights, and driving data-informed strategies that can steer organizations toward success. It is the gatekeeper, granting you access to the realms of data science where innovation and problem-solving are the order of the day.
This benchmark goes far beyond a mere numerical achievement; it should be perceived as a profound symbol of your level of preparedness. It serves as a powerful testament to the fact that you have cultivated a holistic and profound grasp of the statistical intricacies, programming proficiencies, and domain-specific expertise that are pivotal for excelling in the realm of data science. Beyond the technical aspects, this milestone showcases your sharpened problem-solving abilities, which empower you to confront real-world challenges and dilemmas with innovative, data-driven solutions.
Is the perfect union ready for you?
In addition to just technological advancement, it’s crucial for the entire industry to progress towards achieving CMMI Level 4 maturity. However, what’s even more significant is that the industry as a whole must gain a comprehensive understanding of the operational requirements necessary to effectively run their products.
Achieving CMMI Level 4 maturity signifies a higher level of process capability and performance for organizations. It implies that not only the technology but also the underlying processes, systems, and management practices need to be elevated to a point where they are both efficient and consistent. This elevated level of maturity is a reflection of a more mature and disciplined approach to software and product development.
But beyond this technical evolution, it’s equally vital for the industry to have a clear grasp of what it entails to manage and maintain the products they offer. This encompasses understanding customer expectations, support requirements, and the entire product lifecycle. This clarity is essential because it allows businesses to align their resources, strategies, and efforts accordingly.
In essence, reaching CMMI Level 4 is an indication of the industry’s commitment to excellence in software development and project management, but achieving success at this level hinges on a holistic understanding of the product’s full lifecycle and the ability to meet the needs of their customers effectively.
Leave a Reply