Initiating a project to implement a security control is a critical undertaking in any organization’s cybersecurity strategy. However, it often raises a fundamental and seemingly straightforward question: “When can we consider this security control fully implemented?” This query, though seemingly simple, is anything but, as it entails a multifaceted evaluation that requires careful consideration of various elements.
Firstly, the complexity of implementing a security control is often underestimated. It involves not only the deployment of technology or software but also the development of comprehensive policies and procedures, employee training, and the establishment of monitoring mechanisms. Each of these aspects demands time, resources, and expertise.
Furthermore, the effectiveness of a security control is not solely determined by its initial deployment but also by its ongoing maintenance and adaptation. Threat landscapes evolve rapidly, and security controls must continuously adapt to address new vulnerabilities and attack vectors. Therefore, the question of completion extends beyond the initial implementation to encompass ongoing monitoring, maintenance, and potential adjustments.
When it comes to implementing security controls, the approach varies depending on whether the control is a standalone system or part of a hub-spoke model. Understanding the nuances of each scenario is crucial in determining when the implementation can be considered complete and effective.
In the case of a standalone security control, the path to completion is relatively straightforward. To gauge when it’s fully implemented, you need to establish various processes and procedures that ensure the security control can function optimally. This entails tasks such as verifying that the security control is operational, appropriately configured, and most importantly, equipped with the right playbooks for responding to alerts.
However, things become more intricate when the security control operates within a hub-spoke model. In this scenario, you must not only implement the necessary processes and procedures for the hub but also for each spoke. Managing a dynamic scope is where complexities often arise during both the project and operational phases.
One possible solution is to freeze the scope, which can work well during the project phase, especially if the scope changes at a slow pace (less than 2% per month) and the project is relatively short (implemented within 3 months). In such cases, during the operational or Business As Usual (BAU) phase, you may only need to address roughly 6% of the initially defined project scope.
However, if the project phase extends beyond 3 months or the scope changes rapidly, freezing the scope may not be a viable option. This is when dealing with a dynamic scope becomes imperative. For longer project phases, it’s common practice to freeze the scope at the beginning of each month.
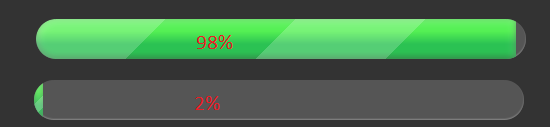
But freezing the scope presents a new challenge: reaching 100% completion may seem nearly impossible. This is where ‘The 98%-rule’ comes into play. According to this rule, 98% of the project scope should be accomplished. Of the remaining 2%, 98% should have a clear explanation and a plan for implementation during the operational phase. The last 2% that lacks a remediation plan should be covered by an approved exception.
Furthermore, ‘The 98%-rule’ can also be applied to the output of the security control. This means that 98% of the generated output should pass a non-repudiation check, and 98% of the generated alerts should be true positives. Achieving this requires implementing processes and procedures to measure the security control’s output at regular intervals, ideally weekly. This frequent assessment, aided by automation, provides early indicators of any issues with the security control’s functionality, allowing for timely adjustments.
Indeed, the concept of ‘The 98%-rule’ may appear ambitious, even somewhat intimidating, particularly for organizations in the initial phases of a project. Nevertheless, it’s crucial to recognize that the underlying intent of this rule is not to create an unattainable standard, but rather to propel security to an elevated status and to infuse it into the very core of an organization’s identity.
At first glance, aiming for a 98% compliance rate with security practices might seem like an insurmountable challenge. Organizations might question whether it’s feasible, especially when dealing with constrained resources or tight timelines. However, the audacious nature of this goal is precisely what makes it so powerful. It serves as a beacon, guiding organizations towards an uncompromising commitment to security.
One must view ‘The 98%-rule’ as an investment rather than a cost. It’s an investment in the long-term resilience and sustainability of the organization. By demanding a high degree of adherence to security standards, it fosters a culture where security isn’t merely an afterthought or an add-on but is deeply ingrained within every facet of the organization’s operations.
The journey towards achieving this 98% compliance rate can be challenging, but it forces organizations to scrutinize their existing processes, identify vulnerabilities, and implement robust security measures. It necessitates proactive risk assessment, continuous improvement, and a willingness to adapt to emerging threats. In essence, it transforms security from being a periodic concern to a continuous, evolutionary process.
Furthermore, the ultimate goal of ‘The 98%-rule’ is not just about meeting a numeric target. It’s about cultivating a mindset where security is not an isolated department or responsibility but a shared commitment across all levels of the organization. It encourages employees to become vigilant stewards of security, reinforcing the idea that protecting sensitive data and digital assets is everyone’s duty.
Leave a Reply