A phishing email is a fraudulent attempt by scammers or cybercriminals to deceive recipients into revealing sensitive information, such as passwords, usernames, credit card details, or personal identification information. These emails are designed to appear as if they are sent by legitimate organizations, such as banks, social media platforms, or e-commerce websites, in order to trick individuals into providing their confidential data. And as phishing emails as a technique has proven to be effective, the adversaries will continue dispatching them. So, the question is what can you do to protect yourself? In this article, I give some tips on how to deal with phishing emails.
What is phishing email?
Phishing emails often mimic the visual design and branding of reputable companies, making them appear convincing and trustworthy. They typically employ social engineering techniques to exploit human vulnerabilities, such as curiosity, fear, or urgency, to prompt recipients to take immediate action without questioning the authenticity of the email. Phishing emails may contain various elements to deceive recipients, including:
- False pretenses: The email may claim to be a security notice, account verification request, financial transaction alert, or prize notification. Scammers use various pretexts to create a sense of urgency or importance, compelling individuals to disclose their information promptly.
- Links to fraudulent websites: Phishing emails often contain links that direct recipients to fake websites that closely resemble the legitimate organization’s website. These websites are designed to collect sensitive information entered by victims, such as login credentials or credit card details.
- Malicious attachments: Some phishing emails may include attachments, such as PDFs, Word documents, or ZIP files, that contain malware or viruses. Opening these attachments can compromise the recipient’s computer or device.
- Email spoofing: Scammers can manipulate the “From” field in the email header to make it appear as if the email is sent from a reputable organization, even though it originates from a different source. This technique is known as email spoofing and aims to trick recipients into believing the email is legitimate.
To protect yourself from phishing emails, it is important to be cautious and vigilant. Look out for suspicious email addresses, double-check URLs before clicking on them, avoid providing personal information through email unless you are certain of its legitimacy, and regularly update your security software. Additionally, report any suspected phishing emails to the relevant organization or authorities to help prevent others from falling victim to such scams.
Phishing emails often exhibit several common characteristics that can help you identify and recognize them. Here are some typical characteristics of phishing emails:
- Sender’s email address: Phishing emails often use email addresses that mimic legitimate organizations or individuals but contain slight variations or misspellings. Pay close attention to the email address, as scammers try to make it appear genuine at first glance.
- Urgency or fear-inducing language: Phishing emails often create a sense of urgency or fear to prompt immediate action. They may claim that your account is compromised, your payment is overdue, or you have won a prize, urging you to respond quickly without much thought.
- Request for personal information: Phishing emails typically ask for sensitive personal information such as passwords, usernames, credit card details, or social security numbers. Legitimate organizations usually do not ask for such information via email.
- Generic greetings: Phishing emails may use generic greetings like “Dear Customer” or “Dear Account Holder” instead of addressing you by your name. This is done because scammers often send mass emails and do not have specific information about the recipients.
- Poor grammar and spelling errors: Phishing emails often contain grammar or spelling mistakes. While legitimate organizations can make mistakes too, frequent errors in a message can be a red flag.
- Suspicious links or attachments: Phishing emails often contain links that direct you to fraudulent websites or attachments that may contain malware. Hover over the link without clicking to see the actual URL, and exercise caution when opening attachments, especially if you were not expecting them.
- Sense of secrecy or exclusivity: Phishing emails may claim to offer confidential or exclusive information, making you feel privileged or special. They might state that you are among a select few chosen for an opportunity or reward.
- Poorly branded or inconsistent design: Phishing emails may use logos, graphics, or overall design that look slightly off or inconsistent with the legitimate organization they are imitating. Pay attention to these visual cues.
- Unusual email content or unexpected emails: Be cautious if you receive an email that seems unexpected or unrelated to your usual interactions with a company or organization. Scammers often send emails randomly or based on harvested email addresses.
It’s important to note that scammers are constantly evolving their tactics, so not all phishing emails will exhibit these characteristics. If you suspect an email to be a phishing attempt, it’s best to verify its authenticity through a separate and trusted communication channel with the organization in question.
Subject: Urgent! Verify Your Account Information Immediately!
Dear Customer,
We regret to inform you that your account has been compromised and requires
immediate action. To secure your account and prevent unauthorized access,
please click the link below to verify your account information:
[Phishing Link]
Failure to complete the verification process within 24 hours will result in
permanent account suspension. We take your security seriously, and it is
imperative that you act swiftly.
Thank you for your cooperation.
Sincerely,
The Account Security Team
The example above several of these phishing indicators can easily be recognized.
- Generic greeting: The email begins with a generic salutation (“Dear Customer”) rather than addressing you by your name. Legitimate organizations usually personalize their communications.
- Urgency and fear tactics: The email creates a sense of urgency and fear by claiming that your account has been compromised and emphasizes immediate action. Phishing emails often employ such tactics to pressure recipients into acting without thinking.
- Suspicious link: The email contains a clickable link that supposedly leads to a verification process. However, in phishing emails, the provided link usually directs you to a fraudulent website designed to collect your personal information. Hovering over the link (without clicking) may reveal a suspicious or unrelated URL.
- Impersonal email signature: The email concludes with a generic closing and does not provide specific contact information or a personal signature. Legitimate organizations typically include more detailed and personalized signatures.
The more advanced/skilled teams know these easy to spot characteristics and therefore, will avoid them. Although the sense of urgency is still an easy to spot red flag, it is becoming more difficult to spot it.
Subject: Important Account Notice: Action Required Dear [Your Name], Due to recent security upgrades, we need you to review and update your account information immediately. Failure to do so may result in account suspension or limited access. To proceed with the update, please click the link below: [Phishing Link] We take your privacy and security seriously, and this update is part of our ongoing commitment to protecting your account. Rest assured that your information will be handled with utmost confidentiality. Thank you for being a valued customer. Sincerely, The Account Services Team
9 Tips when dealing with phishing emails
Tip 1: SPF and DMARC
Luckily, the server who received the phishing can help with spotting phishing emails as most of these emails have issues with DMARC and SPF. These are email authentication mechanisms that can help combat phishing emails and protect against email spoofing.
- Sender Policy Framework (SPF): SPF is an email authentication protocol that allows domain owners to specify which mail servers are authorized to send emails on behalf of their domain. SPF records are DNS (Domain Name System) records that list the authorized email servers. When an email is received, the recipient’s email server checks the SPF record of the sender’s domain to verify if the sending server is allowed to send emails for that domain. If the SPF check fails, it indicates a potential spoofing attempt or unauthorized sender.
- Domain-based Message Authentication, Reporting, and Conformance (DMARC): DMARC builds upon SPF and adds another layer of email authentication. It allows domain owners to specify how receiving email servers should handle emails that fail SPF or DKIM (DomainKeys Identified Mail) checks. With DMARC, domain owners can set policies to specify whether to reject, quarantine, or allow emails that fail authentication. DMARC also provides reporting mechanisms that enable domain owners to receive feedback and insights on email authentication failures and attempts to impersonate their domain.
Implementing SPF and DMARC can significantly enhance email security and help reduce the likelihood of phishing emails:
- SPF helps validate the authenticity of the sending server by checking if it is authorized to send emails for the domain.
- DMARC provides instructions to receiving email servers on how to handle emails that fail authentication, such as marking them as spam or rejecting them outright.
By deploying SPF and DMARC records and configuring them correctly, domain owners can strengthen their email authentication and make it more difficult for attackers to spoof their domain, reducing the risk of phishing emails appearing to come from their domain.
However, it’s important to note that SPF and DMARC are not foolproof solutions and require proper configuration and ongoing monitoring to be effective. They work in conjunction with other security measures, user awareness, and best practices to combat phishing and email spoofing effectively.
But still, some users will still click on these links. According to the 2020 Verizon Data Breach Investigations Report, about 3% of users click on a phishing link within a phishing campaign. However, it’s worth noting that these numbers can fluctuate and may be different in specific contexts or industries. For this reason, it is important to have a next layer of defense.
Tip 2: User awareness
The effectiveness of phishing attacks often relies on social engineering techniques, such as creating a sense of urgency, fear, or curiosity, and manipulating human psychology to persuade recipients to take action. Attackers continuously adapt their tactics to increase their success rates, making it crucial for individuals and organizations to maintain a high level of awareness and adopt security measures to mitigate the risks associated with phishing attacks.
Educating users about the dangers of phishing, implementing strong technical security controls, and regularly testing and improving email filtering systems can help reduce the click rates and overall success of phishing attempts.
Tip 3: User and Entity Behavior Analytics
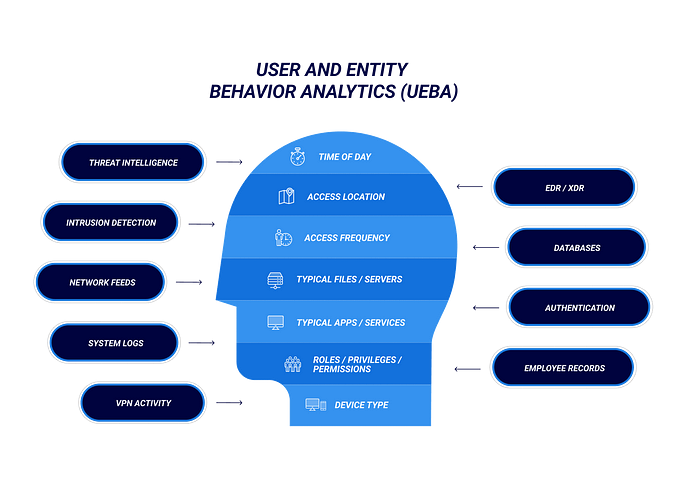
User Behavior Analytics (UBA) can be a valuable tool in detecting and mitigating phishing emails. UBA focuses on analyzing user behavior patterns, such as login activity, email interactions, and application usage, to establish baseline behavior and identify anomalies or suspicious activities that may indicate a phishing attempt.
Here’s how UBA can help in the context of phishing:
- Flagging unusual email behavior: UBA can monitor users’ email activity and identify anomalies, such as sudden spikes in sending emails to unknown recipients, an unusually high number of emails with attachments, or an increase in emails containing suspicious links. These behaviors can indicate that a user’s account has been compromised or that they are engaging in risky email practices.
- Identifying credential theft: Phishing attacks often aim to steal user credentials. UBA can detect unusual login behavior, such as repeated failed login attempts, logins from unfamiliar locations, or simultaneous logins from multiple geographically distant locations. These indicators may suggest that a user’s credentials have been compromised or that a phishing attack is in progress.
- Assessing response to phishing simulations: Organizations can conduct simulated phishing campaigns to assess users’ susceptibility to phishing attacks. UBA can track users’ responses to these simulations, such as clicking on suspicious links or providing sensitive information, to identify individuals who require additional training or awareness reinforcement.
- Analyzing click-through rates: UBA can monitor users’ click-through rates on email links and compare them to baseline behavior. A sudden increase in click rates on suspicious links can be an indication of a successful phishing attack or compromised user accounts.
By leveraging UBA, organizations can gain insights into user behavior that may indicate phishing attempts and take proactive measures to mitigate the risks. This can include providing targeted user training, implementing additional security controls, or flagging suspicious activities for investigation and response.
It’s important to note that UBA should be used in conjunction with other security measures, such as email filtering, endpoint protection, and user awareness training, to create a comprehensive defense against phishing attacks.
But as written in this blog, User Behavior Analytics is not easy to implement in such a way it brings value. I have seen many implementations fail because the team just thought it is implementing a tool.
Tip 4: Antimalware / Endpoint Detection and Response
Endpoint Detection and Response (EDR) solutions primarily focus on detecting and responding to advanced threats and malicious activities on endpoints, such as workstations, laptops, and servers. While EDR solutions may not directly prevent phishing emails from reaching a user’s inbox, they can provide valuable assistance in mitigating the impact of a successful phishing attack. Here’s how EDR can help against phishing:
- Malicious attachment and link detection: EDR solutions often include capabilities to scan email attachments and URLs for known malware or suspicious indicators. If a user clicks on a malicious link or opens a malicious attachment, the EDR solution can detect and block the subsequent malicious activities on the endpoint.
- Behavior-based detection: EDR solutions monitor endpoint activities and behaviors, looking for signs of malicious activity. In the case of phishing, EDR may detect and block the execution of malicious payloads or processes associated with phishing attacks, such as credential-stealing malware or keyloggers.
- Indicators of compromise (IOCs): EDR solutions can leverage threat intelligence and IOCs to identify known malicious indicators associated with phishing campaigns. This can include known command-and-control (C2) servers, malicious domains, or malicious file hashes. When such IOCs are detected on an endpoint, the EDR solution can trigger alerts or take automated response actions to prevent further damage.
- Incident response and forensics: If a user falls victim to a phishing attack, EDR solutions can help in incident response efforts. They provide visibility into the affected endpoint, allowing security teams to investigate the attack, identify the extent of the compromise, and take appropriate remediation actions.
Tip 5: Microsoft Sysmon

Sysmon (System Monitor) is a Windows-based system monitoring tool provided by Microsoft. While it can be a valuable component of an overall security monitoring strategy, it is not specifically designed to directly prevent or detect phishing emails. However, Sysmon can contribute to the detection and response capabilities in the context of phishing attacks in the following ways:
- Process monitoring: Sysmon captures detailed information about processes running on a system, including their creation, termination, and related network connections. This information can be useful in identifying any suspicious processes or unusual network activity that might be associated with a phishing attack.
- Malware detection: Sysmon can be configured to monitor specific file and registry modifications, which can help identify the presence of malware associated with phishing campaigns. For example, it can track changes to specific system areas where malware might install itself or modify system settings.
- Command-line activity monitoring: Sysmon can capture command-line activity on a system, which can be beneficial in identifying any malicious commands or scripts executed as part of a phishing attack. For example, it can detect the execution of PowerShell commands or the use of obfuscated scripts.
- Event correlation: By integrating Sysmon logs with a SIEM (Security Information and Event Management) solution, security teams can perform correlation analysis and detect patterns or anomalies related to phishing attacks. For example, correlating network connections with email-related processes or unusual command-line activity can help identify potential phishing incidents.
While Sysmon provides valuable insights into system-level activities, it should be used in conjunction with other security measures, such as email filtering, user awareness training, and endpoint protection solutions, to form a comprehensive defense against phishing attacks.
It’s important to note that proper configuration, regular monitoring, and analysis of Sysmon logs are essential to leverage its full potential in detecting and responding to security incidents, including those related to phishing.
Tip 6: Security Information and Event Management
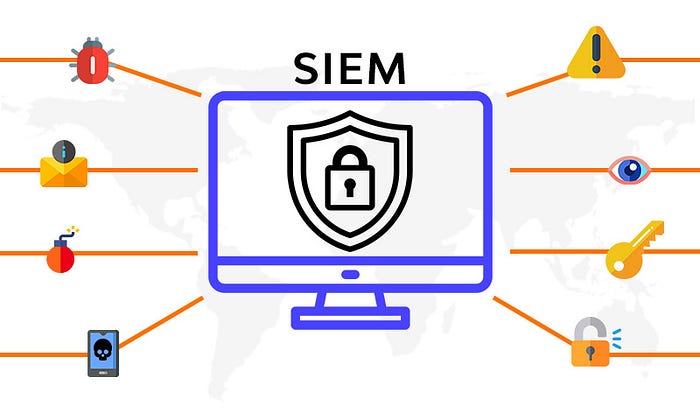
A SIEM (Security Information and Event Management) solution can and should play a significant role in detecting and responding to phishing emails by leveraging its capabilities for log collection, analysis, and correlation.
- Log collection and aggregation: SIEM solutions collect and centralize logs from various sources, including email servers, firewalls, intrusion detection systems (IDS), and endpoint protection solutions. By aggregating email-related logs, SIEM enables comprehensive visibility into email activities and enhances the ability to detect suspicious or malicious behavior.
- Email filtering and detection: SIEM can integrate with email security gateways or filtering solutions to ingest logs and events related to email filtering and detection. This allows for real-time monitoring and analysis of email-related events, such as blocked or quarantined messages, flagged attachments, or suspicious email sender information.
- Phishing pattern and signature detection: SIEM can use pattern matching and signature-based detection mechanisms to identify known phishing indicators. This can include detecting specific email subjects, malicious attachments, or URLs commonly associated with phishing campaigns. SIEM can generate alerts or trigger automated response actions based on these detections.
- User behavior monitoring: SIEM can monitor user behavior related to email activities, such as abnormal email forwarding, mass distribution of emails, or bulk email deletions. Unusual patterns or deviations from normal behavior can indicate a compromised account or a phishing attempt. SIEM can generate alerts or apply user behavior analytics to identify such anomalies.
- Correlation and threat intelligence: SIEM solutions excel at correlating events and logs from various sources. By correlating email-related events with other security events, such as failed logins, network traffic anomalies, or malware detections, SIEM can identify potential indicators of a phishing attack. Additionally, SIEM can leverage threat intelligence feeds to compare email-related events against known phishing indicators or suspicious IP addresses.
- Incident response and investigation: SIEM provides valuable capabilities for incident response and investigation of phishing incidents. It enables security teams to trace the origin of a phishing email, identify affected users, and determine the extent of the compromise. SIEM’s historical log data and analysis tools can assist in post-incident analysis and forensics.
Tip 7: Email filtering

Phishing email filtering refers to the process of identifying and blocking or flagging emails that are designed to deceive recipients and trick them into divulging sensitive information or performing harmful actions. Phishing emails are typically disguised as legitimate messages from trustworthy sources, such as banks, social media platforms, or government agencies, but they aim to steal personal information, login credentials, or financial details.
Phishing email filtering involves employing various techniques and technologies to detect and mitigate phishing attempts. Here are some common methods used in phishing email filtering:
- Content Analysis: Phishing filters analyze the content of incoming emails, looking for indicators of phishing activity. These filters examine the email’s headers, subject lines, body text, and embedded links to identify suspicious patterns, keywords, or URLs associated with known phishing attacks.
- Sender Authentication: Phishing filters verify the sender’s identity by checking the email’s headers and digital signatures. They compare the sender’s information with trusted databases, such as Sender Policy Framework (SPF), DomainKeys Identified Mail (DKIM), and Domain-based Message Authentication, Reporting, and Conformance (DMARC), to determine if the email is legitimately sent from the claimed source.
- Reputation Analysis: Phishing filters assess the reputation of the sender’s domain, IP address, or email service provider. If the sender’s reputation is associated with previous phishing activities or spamming, the email may be flagged or blocked.
- Link Analysis: Phishing filters inspect the links embedded within emails to determine if they redirect to known phishing websites. They compare the URL against a database of known phishing sites or use real-time analysis to assess the site’s reputation and safety.
- Image Analysis: Phishing emails often contain images with embedded URLs or malicious code. Filters can analyze these images to identify hidden links or malicious payloads.
- Machine Learning: Advanced phishing filters leverage machine learning and artificial intelligence algorithms to continuously improve their ability to detect new and evolving phishing techniques. They learn from patterns and characteristics of known phishing attacks and adapt to new threats.
When a phishing email is detected, filtering systems can take various actions, such as quarantining the message, flagging it as potentially dangerous, or blocking it outright. Some email providers also rely on user feedback to improve their filtering algorithms, allowing users to report suspected phishing emails, which contributes to enhancing the overall filtering effectiveness.
Tip 8: Multi Factor Authentication

Multi-factor authentication (MFA) is a security measure that adds an extra layer of protection to your online accounts. It requires users to provide multiple pieces of evidence to verify their identity, typically combining something they know (e.g., a password), something they have (e.g., a mobile device or hardware token), or something they are (e.g., biometric data like a fingerprint or facial recognition).
Phishing emails, on the other hand, are fraudulent messages designed to trick recipients into revealing sensitive information or performing actions that may compromise their security. Phishing emails often appear to come from reputable sources, such as banks, social media platforms, or well-known companies, but they are actually sent by malicious actors.
The connection between multi-factor authentication and phishing emails lies in the fact that MFA can help protect against the risks posed by phishing attacks. Even if a user falls victim to a phishing email and unknowingly provides their username and password, MFA can prevent unauthorized access to their account because the attacker would still need the additional factor to complete the authentication process.
For example, let’s say you receive a phishing email claiming to be from your bank, asking you to click on a link and enter your login credentials. If you were to fall for the scam and enter your username and password, the attacker would still need the second factor (e.g., a code sent to your phone) to successfully authenticate and gain access to your account. Without that additional factor, the attacker would be thwarted by the multi-factor authentication system.
It’s important to note that while MFA is an effective security measure, it is not foolproof. Phishing attacks can sometimes be sophisticated, and attackers may employ various tactics to try to bypass or trick users into providing all the necessary authentication factors. Therefore, it’s crucial to remain vigilant and follow best practices for recognizing and avoiding phishing attempts, such as verifying the legitimacy of emails and never clicking on suspicious links or providing personal information unless you are certain of the sender’s authenticity.
Tip 9: Be ready for when a phishing email is successful
It is true that despite the security controls and processes in place, the constantly evolving nature of phishing attacks means that there is always a possibility of a successful attempt. Adversaries are indeed persistent in their efforts to bypass defenses and exploit vulnerabilities. However, implementing effective security measures can significantly reduce the likelihood of falling victim to phishing attacks and mitigate potential damages.
When responding to a successful phishing email, it’s crucial to take immediate action to minimize the potential impact and prevent further compromise. Here are some steps to follow for an effective incident response:
- Conduct a post-incident analysis: Perform a thorough investigation into the incident to understand how the phishing email bypassed security measures and identify any vulnerabilities in your organization’s defenses. This analysis will help improve your incident response procedures and enhance security measures.
- Identify and isolate: Determine which individual or account was targeted by the phishing email. If it was sent to multiple recipients, identify all affected parties. Quarantine the affected system or account to prevent any further damage or unauthorized access.
- Notify relevant parties: Inform the affected user(s) and their immediate supervisor or manager about the incident. Additionally, notify your organization’s IT or security team, as they will play a vital role in the incident response process.
- Secure compromised accounts: If an account has been compromised, immediately change the password and enable multi-factor authentication (MFA) to prevent unauthorized access. Review the account’s settings and ensure that no suspicious rules or forwarding addresses have been added.
- Preserve evidence: Preserve any evidence related to the phishing email, such as the email itself, email headers, and any attachments. This evidence may be useful for forensic analysis and future investigations.
- Assess the scope and impact: Determine the extent of the phishing attack. Has any sensitive data been exposed or compromised? Assess the potential impact on systems, networks, or confidential information.
- Mitigate the attack: Take immediate steps to mitigate the impact of the phishing attack. This may include removing malicious emails from inboxes, updating security configurations, or blocking the sender’s email address or domain.
Leave a Reply